问题,要求,监控需要进行加密传输,确保数据安全,如无法使用nrpe,请参考
博客另外一篇文章
nsclient++ 使用check_nrpe监控windos
本文采用TSL方式来加密
说明:
我的测试环境没有真正的CA服务器,所有这里我们用Nagios服务器作为CA服务器,
正式部署是请使用专门的CA服务器。
正式创建准备
[root@nagios ~]# mkdir -p -m 750 /usr/local/nagios/etc/ssl
[root@nagios ~]# chown root.nagios /usr/local/nagios/etc/ssl
[root@nagios ~]# cd /usr/local/nagios/etc/ssl/
[root@nagios ssl]# mkdir -m 750 ca nagios_server_certs client_certs
[root@nagios ssl]# chown root.root ca
[root@nagios ssl]# chown root.nagios nagios_server_certs client_certs
[root@nagios ssl]# touch /etc/pki/CA/index.txt
[root@nagios ssl]# echo '1000' > /etc/pki/CA/serial
[root@nagios ssl]# cd /usr/local/nagios/etc/ssl/ca/
创建CA正式
[root@nagios ca]# openssl req -x509 -newkey rsa:4096 -keyout ca_key.pem -out ca_cert.pem -utf8 -days 3650
Generating a 4096 bit RSA private key
......................................................................................................................................................++
........................................................................................................................................................++
writing new private key to 'ca_key.pem'
Enter PEM pass phrase:**********
Verifying - Enter PEM pass phrase:**********
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:BeiJing
Locality Name (eg, city) [Default City]:ChaoYang
Organization Name (eg, company) [Default Company Ltd]:Nec
Organizational Unit Name (eg, section) []:Monitoring
Common Name (eg, your name or your server's hostname) []:Nagios
Email Address []:nagios@nagioschina.club
[root@nagios ca]#
以上红色标记的部分为输入部分,根据自己的情况输入,完成后会在目录下生成两个文件
创建客户端证书
[root@nagios ca]# cd /usr/local/nagios/etc/ssl/client_certs/
[root@nagios client_certs]# openssl req -new -newkey rsa:2048 -keyout client_cert.key -out client_cert.csr -nodes
Generating a 2048 bit RSA private key
...................+++
...............+++
writing new private key to 'client_cert.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:BeiJing
Locality Name (eg, city) [Default City]:ChaoYang
Organization Name (eg, company) [Default Company Ltd]:Nec
Organizational Unit Name (eg, section) []:Monitoring
Common Name (eg, your name or your server's hostname) []:WindosClient
Email Address []:nagios@nagioschina.club
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []: //这里不输入,直接回车
An optional company name []: //同上
[root@nagios client_certs]#
使用CA证书认证生成的客户端证书
[root@nagios client_certs]# cd /usr/local/nagios/etc/ssl/
[root@nagios ssl]# openssl ca -days 365 -notext -md sha256 -keyfile ca/ca_key.pem -cert ca/ca_cert.pem -in client_certs/client_cert.csr -out client_certs/client_cert.pem
Using configuration from /etc/pki/tls/openssl.cnf
Enter pass phrase for ca/ca_key.pem:********** //输入创建CA证书设置的密码
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4096 (0x1000)
Validity
Not Before: Aug 15 02:06:42 2017 GMT
Not After : Aug 15 02:06:42 2018 GMT
Subject:
countryName = CN
stateOrProvinceName = BeiJing
organizationName = Nec
organizationalUnitName = Monitoring
commonName = WindosClient
emailAddress = nagios@nagioschina.club
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
79:46:54:03:52:07:58:B7:1C:9A:71:A1:B0:FD:72:E9:1E:F9:56:C4
X509v3 Authority Key Identifier:
keyid:99:FE:BF:D2:4F:E9:F6:1D:34:A4:98:78:A7:8A:25:44:47:0C:0B:52
Certificate is to be certified until Aug 15 02:06:42 2018 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@nagios ssl]#
执行完成后会生成两个文件
client_certs/client_cert.pem
client_certs/client_cert.key
需要把以上的两个文件和CA文件ca/ca_cert.pem拷贝到客户端上目录如下,C:\Program Files\NSClient++\security
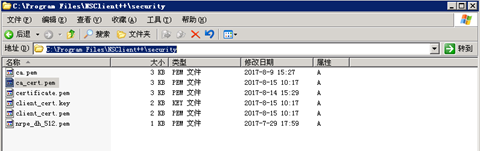
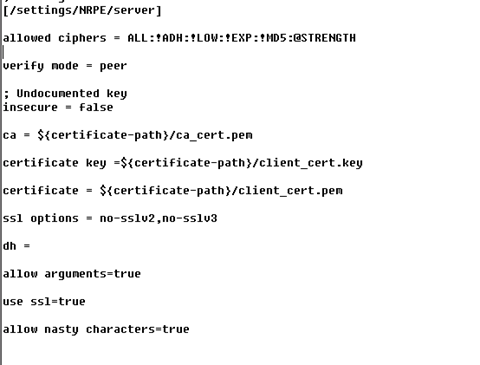
nsclient++配置如下,
[/settings/NRPE/server]
allowed ciphers = ALL:!ADH:!LOW:!EXP:!MD5:@STRENGTH
verify mode = peer
insecure = false
ca = ${certificate-path}/ca_cert.pem
certificate key =${certificate-path}/client_cert.key
certificate = ${certificate-path}/client_cert.pem
ssl options = no-sslv2,no-sslv3
dh =
allow arguments=true
use ssl=true
allow nasty characters=true
服务器证书创建,和创建客户端证书一样
[root@nagios ssl]# cd /usr/local/nagios/etc/ssl/nagios_server_certs/
[root@nagios nagios_server_certs]# openssl req -new -newkey rsa:2048 -keyout nagios_server.key -out nagios_server.csr -nodes
Generating a 2048 bit RSA private key
........................+++
..................................................+++
writing new private key to 'nagios_server.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:BeiJing
Locality Name (eg, city) [Default City]:ChaoYang
Organization Name (eg, company) [Default Company Ltd]:nEC
Organizational Unit Name (eg, section) []:Monitoring
Common Name (eg, your name or your server's hostname) []:Nagios_Server
Email Address []:nagios@nagioschina.club
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []: //这里不输入,直接回车
An optional company name []: //这里不输入,直接回车
[root@nagios nagios_server_certs]#
使用CA签发服务器证书
[root@nagios nagios_server_certs]# cd /usr/local/nagios/etc/ssl/
========报错啦====================
Using configuration from /etc/pki/tls/openssl.cnf
Enter pass phrase for ca/ca_key.pem:
Check that the request matches the signature
Signature ok
The organizationName field needed to be the same in the
CA certificate (Nec) and the request (nEC)
马虎了在输入组织名称时开着大写输入错误了,删掉重新创建服务器端证书。
==============================
步骤和客户端一样
[root@nagios ssl]# openssl ca -days 365 -notext -md sha256 -keyfile ca/ca_key.pem -cert ca/ca_cert.pem -in nagios_server_certs/nagios_server.csr -out nagios_server_certs/nagios_server.pem
Using configuration from /etc/pki/tls/openssl.cnf
Enter pass phrase for ca/ca_key.pem:********** //输入创建CA证书设置的密码
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4097 (0x1001)
Validity
Not Before: Aug 15 02:34:04 2017 GMT
Not After : Aug 15 02:34:04 2018 GMT
Subject:
countryName = CN
stateOrProvinceName = BeiJing
organizationName = Nec
organizationalUnitName = Monitoring
commonName = Nagios_server
emailAddress = nagios@nagioschina.club
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
38:78:9C:6D:F5:D4:BA:6A:AB:D2:76:DE:23:82:56:9D:69:FC:37:52
X509v3 Authority Key Identifier:
keyid:99:FE:BF:D2:4F:E9:F6:1D:34:A4:98:78:A7:8A:25:44:47:0C:0B:52
Certificate is to be certified until Aug 15 02:34:04 2018 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@nagios ssl]#
和客户端证书一样会生成两个文件
nagios_server_certs/nagios_server.pem
nagios_server_certs/nagios_server.key
Check_nrpe 验证
[root@nagios ssl]# /usr/local/nagios/libexec/check_nrpe -A /usr/local/nagios/etc/ssl/ca/ca_cert.pem -C /usr/local/nagios/etc/ssl/nagios_server_certs/nagios_server.pem -K /usr/local/nagios/etc/ssl/nagios_server_certs/nagios_server.key -H 172.19.1.177
I (0.5.1.39 2017-07-30) seem to be doing fine...
[root@nagios ssl]#
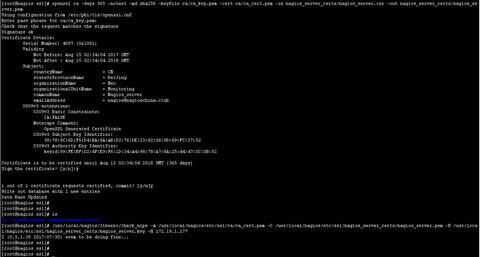
也可以写入到文件中在调用,把相关的命令写入到配置文件中
[root@nagios libexec]# echo "-C /usr/local/nagios/etc/ssl/nagios_server_certs/nagios_server.pem" >>/usr/local/nagios/libexec/check_nrpe.conf
[root@nagios libexec]# echo "-K /usr/local/nagios/etc/ssl/nagios_server_certs/nagios_server.key" >>/usr/local/nagios/libexec/check_nrpe.conf
[root@nagios libexec]# echo "-A /usr/local/nagios/etc/ssl/ca/ca_cert.pem" >>/usr/local/nagios/libexec/check_nrpe.conf
[root@nagios libexec]# echo "-2" >>/usr/local/nagios/libexec/check_nrpe.conf
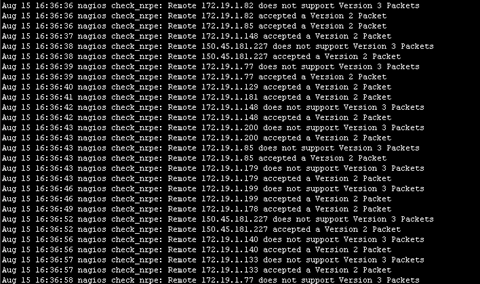
-2使用nrpe版本协议进行数据传输,nsclient++不支持版本3的数据。不加这项日志会有以下信息刷屏,对排错不好
Aug 15 16:36:43 nagios check_nrpe: Remote 172.19.1.179 does not support Version 3 Packets
Aug 15 16:36:43 nagios check_nrpe: Remote 172.19.1.179 accepted a Version 2 Packet
Aug 15 16:36:46 nagios check_nrpe: Remote 172.19.1.199 does not support Version 3 Packets
Aug 15 16:36:46 nagios check_nrpe: Remote 172.19.1.199 accepted a Version 2 Packet
Aug 15 16:36:49 nagios check_nrpe: Remote 172.19.1.178 accepted a Version 2 Packet
Aug 15 16:36:52 nagios check_nrpe: Remote 150.45.181.227 does not support Version 3 Packets
Aug 15 16:36:52 nagios check_nrpe: Remote 150.45.181.227 accepted a Version 2 Packet
Aug 15 16:36:56 nagios check_nrpe: Remote 172.19.1.140 does not support Version 3 Packets
Aug 15 16:36:56 nagios check_nrpe: Remote 172.19.1.140 accepted a Version 2 Packet
Aug 15 16:36:57 nagios check_nrpe: Remote 172.19.1.133 does not support Version 3 Packets
Aug 15 16:36:57 nagios check_nrpe: Remote 172.19.1.133 accepted a Version 2 Packet
Aug 15 16:36:58 nagios check_nrpe: Remote 172.19.1.77 does not support Version 3 Packets
使用配置文件有两种方式,当然是加-f参数比较方便
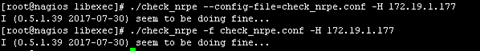
下一步我们添加到Nagios命令文件这个不说步骤了
define command {
command_name check_nrpe_windos
command_line $USER1$/check_nrpe_v3 -f check_nrpe.conf -H $HOSTADDRESS$ -c $ARG1$ $ARG2$
register 1
}
我这里使用的check_nrpe_v3,是另外安装的一个nrpe3.2版本,以前安装的为3.1版本,
如何验证证书是否正常使用
在Nsclient++中修改verify mode 认证模式,对端认证,
verify mode = peer,fail-if-no-cert
返回客户端使用命令查看就会发现结果,不使用证书时无法正常连接
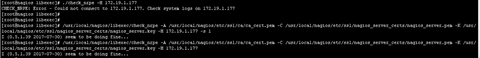
使用-S 验证加密类型 -S TLSv1.2+ ,时支持TLS安全协议的
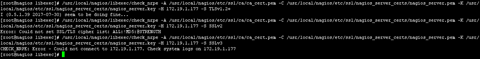
把nsclent+++的证书相关选项去掉,插件也无法正常工作
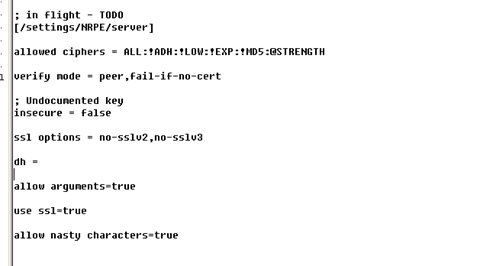
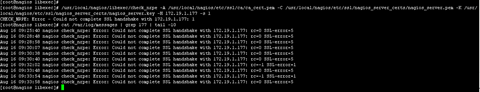
好了加密说明就到这里了。当然使用无法认证的正式,两边的通信也是无法正常建立的
文章末尾固定信息



评论